In today's digital age, cybersecurity has become an essential aspect of our lives, with technology playing a vital role in almost every industry. As our reliance on technology grows, so does the need for robust cybersecurity measures to protect our sensitive information and systems from potential threats. However, the question remains: how difficult is cybersecurity, and what does it entail? Let's delve into the world of cybersecurity and explore its complexities.
Understanding Cybersecurity

Cybersecurity, often referred to as information technology security, is the practice of protecting computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks, damage, or unauthorized access. It encompasses a wide range of techniques, technologies, and processes designed to ensure the confidentiality, integrity, and availability of information and systems.
The primary goal of cybersecurity is to mitigate the risks associated with cyber threats and ensure the smooth operation of digital infrastructure. With the increasing sophistication of cyber attacks, it has become imperative for individuals, organizations, and governments to prioritize cybersecurity to safeguard their digital assets and maintain trust in the digital realm.
The Challenges of Cybersecurity

Cybersecurity is a complex field that presents numerous challenges, making it a highly demanding and dynamic profession. Here are some key challenges that cybersecurity professionals face:
-
Ever-Evolving Threats: The landscape of cyber threats is constantly evolving, with new vulnerabilities and attack techniques emerging regularly. Cybersecurity professionals must stay updated with the latest trends, methodologies, and technologies to effectively counter these threats.
-
Skill Shortage: The demand for skilled cybersecurity professionals far exceeds the supply, creating a significant talent gap. This shortage makes it challenging for organizations to find and retain the right talent to build a robust cybersecurity team.
-
Complex Infrastructure: Modern organizations often have complex IT infrastructures, consisting of various interconnected systems and networks. Securing such diverse environments requires a deep understanding of network architecture, system administration, and potential vulnerabilities.
-
Human Factor: Despite implementing robust technical measures, human error remains a significant factor in cybersecurity breaches. Educating users about safe practices and raising awareness about potential threats is crucial to minimize the risk of successful attacks.
-
Regulatory Compliance: With the introduction of data privacy regulations like GDPR and CCPA, cybersecurity professionals must ensure compliance with these laws to avoid legal consequences and maintain public trust.
The Role of Cybersecurity Professionals

Cybersecurity professionals play a crucial role in safeguarding digital assets and ensuring the resilience of organizations against cyber threats. Here are some key responsibilities and skills associated with this field:
Responsibilities

-
Threat Intelligence: Cybersecurity professionals must stay ahead of the curve by gathering and analyzing threat intelligence. This involves monitoring emerging threats, understanding attack vectors, and developing strategies to mitigate potential risks.
-
Vulnerability Assessment: Regularly conducting vulnerability assessments is essential to identify weaknesses in an organization's systems and networks. These assessments help prioritize and address potential security gaps.
-
Incident Response: In the event of a security breach, cybersecurity professionals are responsible for implementing an effective incident response plan. This includes containing the breach, investigating the root cause, and taking measures to prevent similar incidents in the future.
-
Security Awareness Training: Educating employees and users about cybersecurity best practices is a critical aspect of an organization's defense strategy. Cybersecurity professionals often lead these training sessions to promote a culture of security awareness.
-
Policy Development: Creating and implementing robust cybersecurity policies and procedures is essential to guide an organization's security practices. These policies should cover various aspects, including data protection, access control, and incident response.
Skills

-
Technical Proficiency: Cybersecurity professionals must possess a strong understanding of computer systems, networking, and programming languages. They should be able to identify and analyze vulnerabilities, as well as implement technical solutions to address security concerns.
-
Analytical Thinking: The ability to think critically and analyze complex scenarios is crucial in cybersecurity. Professionals must assess potential risks, evaluate the impact of security incidents, and make informed decisions to mitigate threats.
-
Communication Skills: Effective communication is essential in cybersecurity, as professionals often need to collaborate with various teams and stakeholders. Clear and concise communication ensures that security measures are understood and implemented correctly.
-
Problem-Solving Abilities: Cybersecurity professionals must be adept at problem-solving, as they often encounter unique and complex challenges. The ability to think creatively and develop innovative solutions is highly valued in this field.
-
Continuous Learning: The field of cybersecurity is constantly evolving, and professionals must commit to lifelong learning. Staying updated with the latest technologies, attack methodologies, and industry best practices is essential to remain effective in this dynamic environment.
The Importance of Cybersecurity Awareness

While cybersecurity professionals play a vital role in safeguarding digital assets, it is essential to emphasize the importance of cybersecurity awareness among all users. Here are some key reasons why cybersecurity awareness is crucial:
-
Preventing Human Error: As mentioned earlier, human error is a significant factor in cybersecurity breaches. By raising awareness about potential threats and safe practices, users can become the first line of defense against cyber attacks.
-
Promoting Safe Online Behavior
-
Building a Culture of Security: Cybersecurity awareness programs help create a culture of security within organizations. When employees understand the importance of cybersecurity and their role in maintaining it, they become more vigilant and proactive in protecting sensitive information.
-
Compliance and Reputation: Adhering to cybersecurity best practices and regulations is not only a legal requirement but also essential for maintaining a positive reputation. Organizations that prioritize cybersecurity demonstrate their commitment to protecting customer data and maintaining trust.
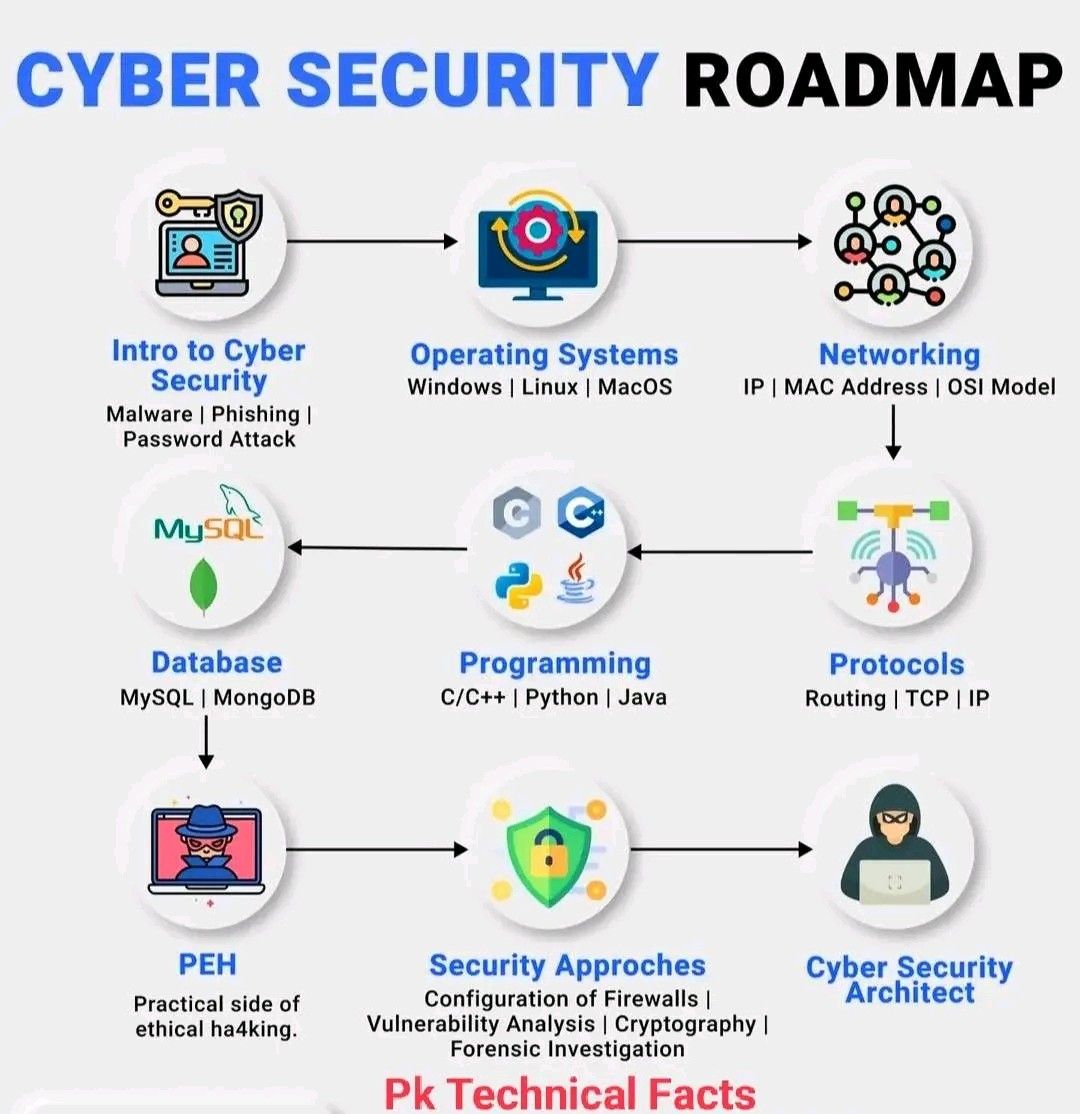
Steps to Enhance Cybersecurity
Implementing effective cybersecurity measures is crucial for individuals and organizations alike. Here are some practical steps to enhance your cybersecurity posture:
For Individuals

-
Use Strong Passwords: Create unique and complex passwords for all your online accounts. Consider using a password manager to generate and store strong passwords securely.
-
Enable Two-Factor Authentication: Adding an extra layer of security through two-factor authentication (2FA) can significantly reduce the risk of unauthorized access to your accounts.
-
Be Cautious with Personal Information: Be mindful of the personal information you share online. Avoid oversharing sensitive details that could be exploited by cybercriminals.
-
Regularly Update Software: Keep your operating systems, browsers, and applications up to date. Software updates often include security patches that address known vulnerabilities.
-
Beware of Phishing Attempts: Be vigilant when receiving emails or messages from unknown sources. Never click on suspicious links or download attachments from untrusted sources.
For Organizations

-
Conduct Regular Security Audits: Schedule periodic security audits to identify vulnerabilities and weaknesses in your systems and networks. Address any critical issues promptly.
-
Implement Access Controls: Restrict access to sensitive data and systems to authorized personnel only. Use strong authentication measures and regularly review user permissions.
-
Encrypt Sensitive Data: Ensure that all sensitive data, both at rest and in transit, is encrypted to protect it from unauthorized access.
-
Invest in Employee Training: Provide comprehensive cybersecurity training to your employees to raise awareness and educate them about potential threats and best practices.
-
Backup Data Regularly: Implement a robust backup strategy to ensure that critical data can be recovered in the event of a security breach or system failure.
The Future of Cybersecurity

As technology continues to advance, the field of cybersecurity is also evolving rapidly. Here are some key trends and predictions for the future of cybersecurity:
-
Artificial Intelligence (AI) and Machine Learning (ML): AI and ML technologies are expected to play a significant role in enhancing cybersecurity. These technologies can automate threat detection, analyze vast amounts of data, and identify patterns to improve security measures.
-
Zero Trust Architecture: The concept of zero trust, which assumes that no user or device should be trusted by default, is gaining traction. This approach requires strict verification and authentication for all users and devices attempting to access an organization's network.
-
Cloud Security: With the increasing adoption of cloud computing, securing cloud-based systems and data will become a top priority for organizations. Cybersecurity professionals will need to develop expertise in cloud security to protect sensitive information stored in the cloud.
-
Quantum Computing: The emergence of quantum computing poses both opportunities and challenges for cybersecurity. While quantum computing can enhance encryption and data protection, it also has the potential to break existing encryption algorithms.
-
Cybersecurity as a Service (CaaS): As the demand for skilled cybersecurity professionals outpaces the supply, organizations are turning to cybersecurity-as-a-service models. This approach allows organizations to outsource their cybersecurity needs to specialized providers.
Conclusion

Cybersecurity is a complex and ever-evolving field that requires a combination of technical expertise, analytical thinking, and a deep understanding of emerging threats. While the challenges are significant, the importance of cybersecurity cannot be overstated in today's digital landscape. By staying vigilant, implementing robust security measures, and raising awareness, individuals and organizations can work together to create a safer digital environment.
As technology continues to advance, so must our cybersecurity practices. Embracing new technologies and staying ahead of emerging threats will be crucial in safeguarding our digital future. Let's continue to prioritize cybersecurity and foster a culture of security awareness to protect our digital assets and maintain trust in the digital realm.
What are the key skills required for a career in cybersecurity?

+
Cybersecurity professionals require a diverse skill set, including technical proficiency in areas such as networking, programming, and operating systems. Analytical thinking, problem-solving abilities, and communication skills are also essential. Additionally, staying updated with the latest technologies and attack methodologies is crucial for success in this field.
How can individuals protect themselves from cyber threats?
+
Individuals can enhance their cybersecurity posture by using strong passwords, enabling two-factor authentication, being cautious with personal information, and regularly updating software. Staying vigilant and aware of potential phishing attempts is also crucial. Additionally, individuals should educate themselves about safe online practices and report any suspicious activities.
What is the role of artificial intelligence in cybersecurity?

+
Artificial intelligence (AI) and machine learning (ML) are expected to play a significant role in enhancing cybersecurity. These technologies can automate threat detection, analyze vast amounts of data, and identify patterns to improve security measures. AI can also assist in incident response and help organizations stay ahead of emerging threats.
How can organizations improve their cybersecurity posture?

+
Organizations can enhance their cybersecurity posture by conducting regular security audits, implementing access controls, encrypting sensitive data, and investing in employee training. Additionally, organizations should stay updated with the latest cybersecurity trends and best practices, and consider outsourcing their cybersecurity needs to specialized providers.
What is the future of cybersecurity?

+
The future of cybersecurity is expected to be shaped by emerging technologies such as artificial intelligence, quantum computing, and cloud security. As technology advances, cybersecurity professionals will need to adapt and stay ahead of evolving threats. Additionally, the concept of zero trust architecture is gaining traction, emphasizing the need for strict verification and authentication in network access.