Identity theft is a serious crime that can have devastating consequences for victims. It involves the unauthorized use of someone's personal information, such as their name, social security number, or financial details, to commit fraud or other illegal activities. Understanding how identity theft occurs is crucial to protecting yourself and your sensitive data. In this blog post, we will explore the various ways identity theft happens and provide insights on how to safeguard your identity.
Common Methods of Identity Theft
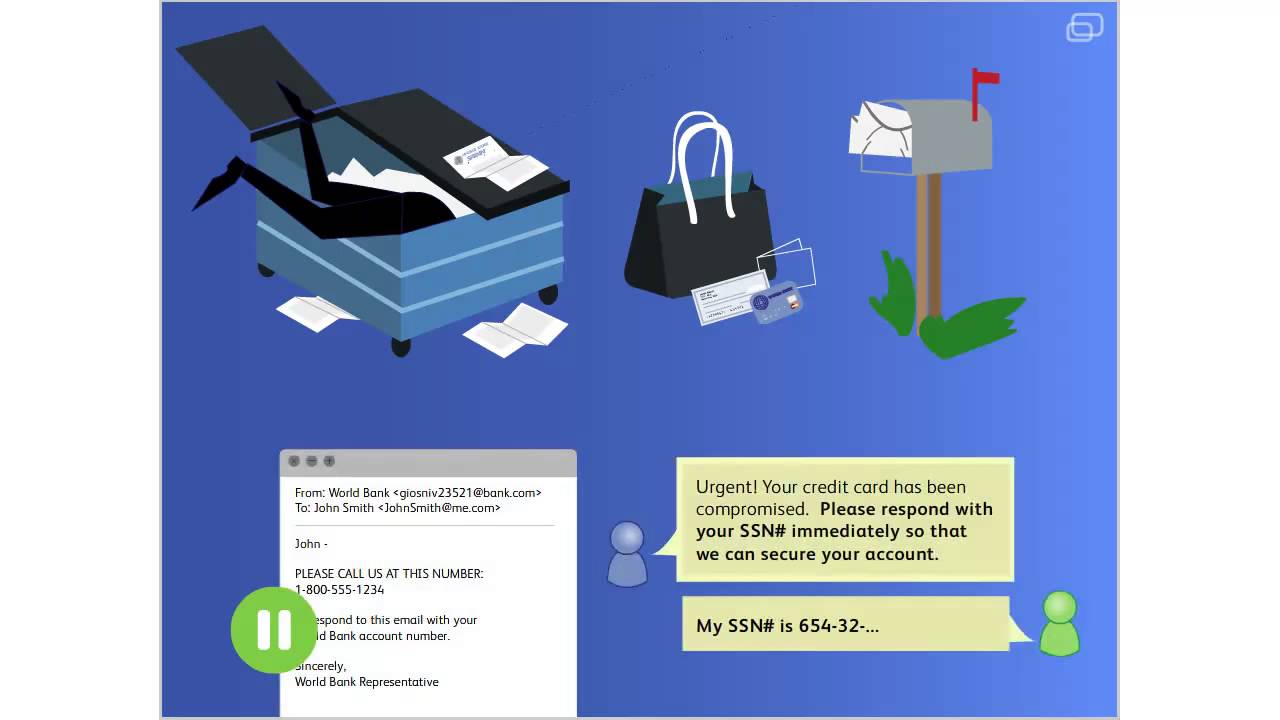
Identity thieves employ numerous tactics to gain access to personal information. Here are some common methods they use:
- Phishing Scams: Phishing is a deceptive practice where scammers send fake emails, text messages, or create fake websites to trick individuals into revealing their personal information. These messages often appear to be from legitimate sources, such as banks or government agencies, and may contain urgent requests or threats to create a sense of panic.
- Skimming: Skimming is a technique used to steal credit or debit card information. Thieves use small devices, called skimmers, to capture the data from the magnetic strip of a card when it is swiped. These skimmers can be hidden in ATMs, gas pumps, or even retail store card readers.
- Data Breaches: Data breaches occur when hackers gain unauthorized access to a company's or organization's database, compromising the personal information of customers or employees. This can include names, addresses, social security numbers, and other sensitive data. Once obtained, this information can be sold on the dark web or used for identity theft.
- Dumpster Diving: Identity thieves may rummage through trash bins in search of discarded documents containing personal information. This includes bank statements, credit card offers, utility bills, or even old tax returns. It is important to shred or properly dispose of sensitive documents to prevent this form of identity theft.
- Social Engineering: Social engineering involves manipulating individuals into revealing their personal information through deception. Thieves may pose as representatives from legitimate organizations, such as banks or tech support, and use persuasive tactics to gain trust and access to sensitive data.
- Public Wi-Fi Risks: Public Wi-Fi networks, such as those found in cafes or airports, can be vulnerable to hacking. Identity thieves can intercept data transmitted over these networks, including login credentials and personal information, if proper security measures are not in place.
Protecting Yourself from Identity Theft

While identity theft can be a challenging issue to address, there are several proactive measures you can take to reduce the risk:
- Be Wary of Phishing Attempts: Always be cautious when receiving unexpected emails or messages requesting personal information. Verify the legitimacy of the sender by contacting the organization directly using official contact details. Avoid clicking on links or downloading attachments from unknown sources.
- Use Secure Payment Methods: When making online purchases, opt for secure payment methods such as credit cards or trusted payment platforms. These methods offer better protection against fraud and unauthorized charges compared to using debit cards or providing sensitive financial information directly.
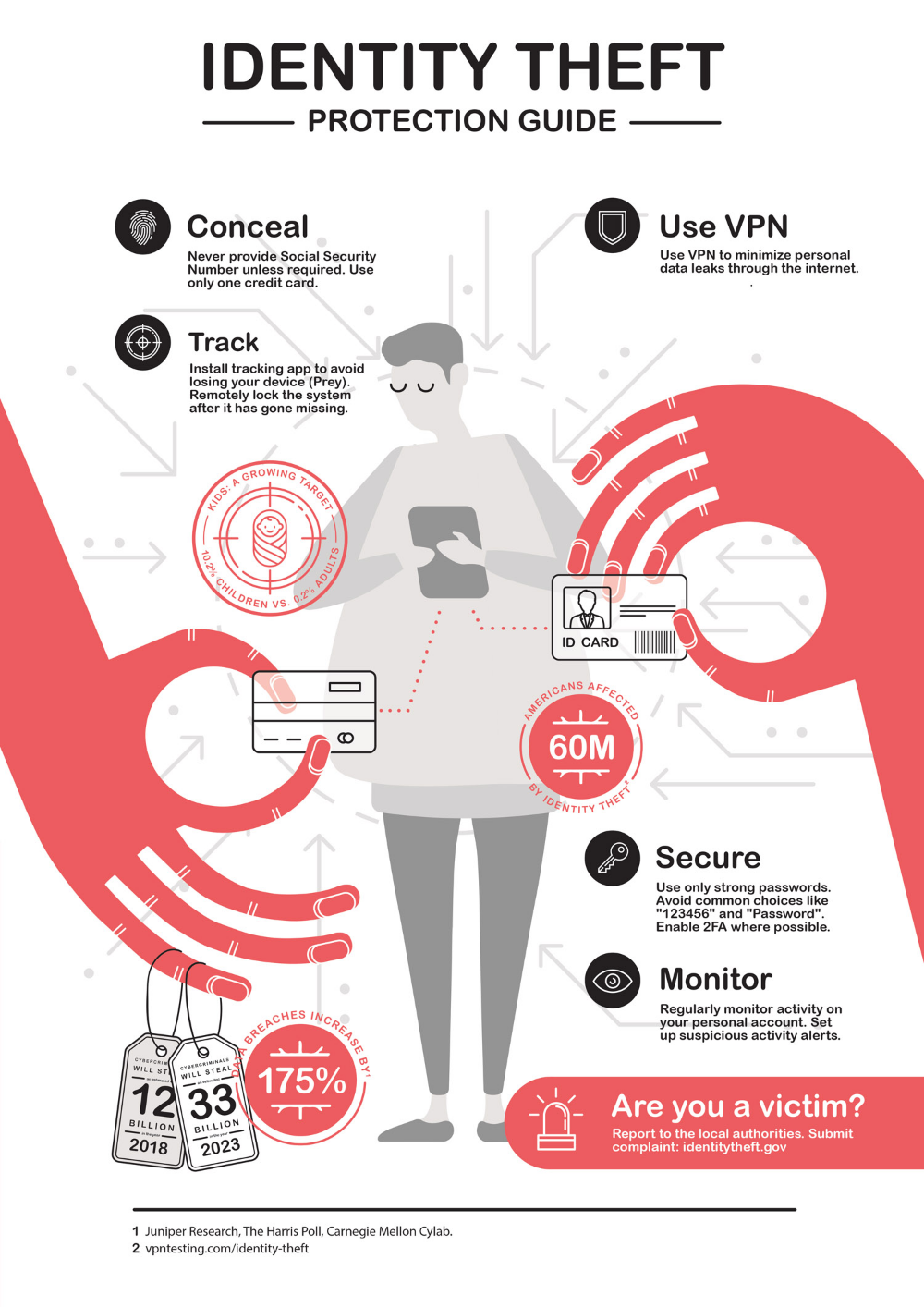
- Monitor Your Credit Reports: Regularly check your credit reports from the major credit bureaus (Equifax, Experian, and TransUnion) to detect any suspicious activities or inaccuracies. Look for unfamiliar accounts, loans, or addresses. If you notice any discrepancies, report them immediately to the respective credit bureau.
- Secure Your Devices: Keep your computers, smartphones, and other devices protected with strong passwords or biometric authentication. Install reputable antivirus software and keep your operating system and applications up to date to prevent malware infections that can lead to identity theft.
- Shred Sensitive Documents: Before discarding documents containing personal information, such as bank statements or tax forms, make sure to shred them properly. Invest in a cross-cut shredder to ensure that the information cannot be reconstructed.
- Use Strong Passwords and Two-Factor Authentication: Create unique and complex passwords for your online accounts. Avoid using easily guessable information like your birthdate or common words. Enable two-factor authentication whenever possible to add an extra layer of security to your accounts.
Steps to Take if Your Identity is Stolen

Despite your best efforts, identity theft can still occur. If you suspect or discover that your identity has been stolen, take the following steps:
- Contact the Authorities: Report the identity theft to your local police department and file a report. This report will serve as evidence and help in the investigation process.
- Inform Financial Institutions: Notify your bank, credit card companies, and other financial institutions about the identity theft. They can help you monitor your accounts for any unauthorized transactions and take appropriate actions to protect your finances.
- Place a Fraud Alert: Contact the credit bureaus and request a fraud alert to be placed on your credit report. This alert will notify potential creditors that you may be a victim of identity theft, making it more difficult for thieves to open new accounts in your name.
- Review Your Credit Reports: Obtain copies of your credit reports from all three major credit bureaus and carefully review them for any inaccurate or fraudulent information. Dispute any errors or unauthorized accounts to have them removed from your credit report.
- Monitor Your Accounts: Keep a close eye on your bank and credit card statements for any suspicious activities. Set up account alerts or notifications to receive real-time updates on transactions. Regularly check your credit score to detect any unusual changes.
Tips for Safe Online Behavior
Practicing safe online habits can significantly reduce the risk of identity theft. Here are some additional tips to consider:
- Use a Virtual Private Network (VPN): When accessing the internet on public Wi-Fi networks, consider using a VPN. A VPN encrypts your internet connection, making it more difficult for hackers to intercept your data.
- Be Selective with Personal Information: Think twice before sharing personal information online, especially on social media platforms. Avoid posting sensitive details such as your full address, phone number, or birthdate publicly.
- Regularly Update Your Software: Keep your operating system, web browsers, and security software up to date. Software updates often include security patches that address vulnerabilities, helping to protect your devices from potential threats.
- Use Secure Websites: When making online transactions, ensure that the website you are using has a valid security certificate. Look for "https" in the website's URL and a padlock icon in the address bar, indicating a secure connection.
- Avoid Public Computers: Refrain from accessing sensitive information or conducting financial transactions on public computers, such as those in internet cafes or libraries. These computers may have malware or keyloggers installed, putting your personal information at risk.
Conclusion

Identity theft is a growing concern in today's digital age, but by staying vigilant and taking proactive measures, you can significantly reduce the risk of becoming a victim. Remember to be cautious with your personal information, regularly monitor your accounts and credit reports, and adopt safe online practices. By following these guidelines, you can better protect your identity and minimize the impact of identity theft.
What should I do if I receive a suspicious email requesting personal information?

+
If you receive a suspicious email asking for personal information, it is best to err on the side of caution. Do not respond to the email or click on any links or attachments. Instead, contact the organization directly using official contact details to verify the legitimacy of the request. If the email is indeed a phishing attempt, report it to the appropriate authorities.
How can I protect my credit card information when making online purchases?

+
When making online purchases, prioritize using secure payment methods such as credit cards or trusted payment platforms. Avoid providing your credit card information directly on websites unless they have a secure payment gateway. Look for the “https” and padlock icon in the website’s URL to ensure a secure connection. Additionally, consider using virtual credit card numbers or one-time-use payment methods for added security.
What are the signs of identity theft?

+
Signs of identity theft can vary, but some common indicators include receiving bills or collection notices for accounts you did not open, noticing unfamiliar charges on your credit card or bank statements, receiving calls or letters about debts you did not incur, or being denied credit despite having a good credit history. It is important to regularly monitor your credit reports and accounts to detect any suspicious activities.
How long does it take to recover from identity theft?

+
The recovery process from identity theft can vary depending on the extent of the theft and the actions taken by the victim. It may take several months or even years to fully restore your credit and financial stability. The process involves reporting the theft to the authorities, working with financial institutions to close fraudulent accounts, disputing inaccurate information on your credit reports, and taking steps to prevent further identity theft.